Introduction
Generally, each individual system has its own independent user system, Comm100 system has its own user system, and other third-party systems also have. Only authenticated users can use many functions and operations in the application.
When we want to break the barriers of the system and use the functions of Comm100 in a third-party system or use the functions of the third-party system in the Comm100, we need to solve the problem of user authentication between different systems.
Comm100 has provided you with a solution. We can extend authentication by configurations in App & Integrations >> Create or manage you own apps >> Edit >> Enable app extended authentication.
Enabling app extended authentication in your Comm100 Account
- Log in to your Comm100 Control Panel and navigate to the App & Integrations module.
- Choose your own app and configure its settings.
- Scroll to bottom, check the Enable app extended authentication option and fill in the required information.
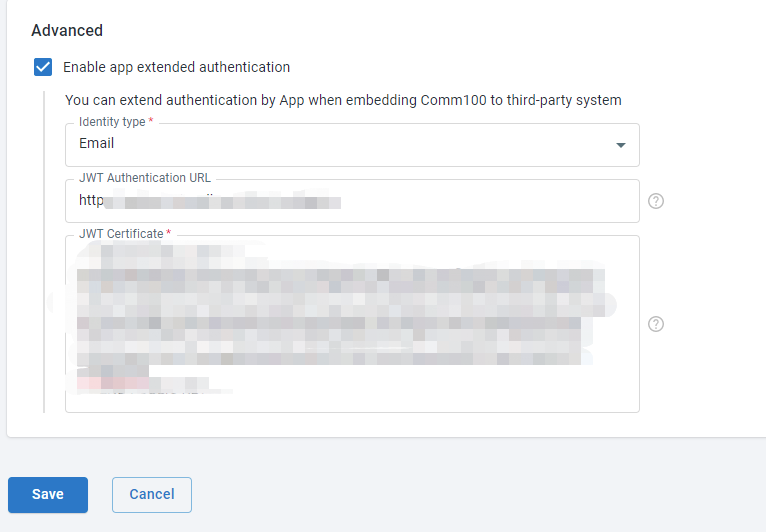
You may have some questions about how to fill in the value, which will be answered in the following article.
How does it work
Unified authentication is performed by configuring SSO in Comm100. So that both the third-party system and Comm100 agent can access the system.
Let's take the Comm100 system embedded in the third-party system as an example to illustrate the process of extending authentication by apps(configured in Comm100, you can think of it as a VoIP system).
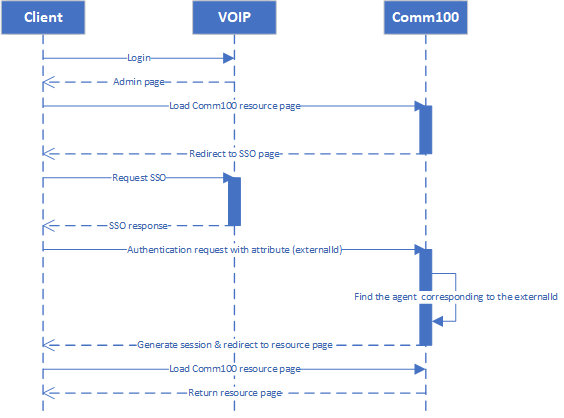
- The VoIP user uses credentials to log in to the VoIP system.
- The VoIP service returns the contents of the page, including Comm100 embedded page.
- Access Comm100 resources and the client browser will use iframes to load Comm100 pages.
- Comm100 redirect the page to SSO page.
- The client browser go to the SSO signon page and starts authenticating.
- Redirect the page to defined JWT Login url.
- The VoIP service verifies whether the current user logs in through the existing session (cookie can be passed because of the same domain).
- VoIP server generates a jwt then redirect the client browser to Comm100.
- Comm100 verifies the signature of the jwt by certificate and reads identifier from the payload to find the corresponding agent.
- Find Comm100 agent corresponding agent and generates session according to the corresponding agent.
- Redirects to the page requested by the user.
Steps for extending authentication by apps
- Creating An APP & Integration
- Preparing necessary information for JWT certification
- Completing app extended authentication configuration in your Comm100 Account
- Adding Comm100 into your app
- Logging into your app and access Comm100 resource.
Creating an App & Integration
If you already know and have created an app, please continue to read it. Otherwise, you can check article Create your own apps for more information.
Preparing necessary information for JWT certification
After we create the app, we can implement extended authentication through Comm100 Agent SSO.
Comm100 Agent SSO allows your agents to have a single login across Comm100 and other applications. You only need to log in once and can move swiftly between Comm100 and other applications without the need to log into separate accounts or remember multiple usernames and passwords.
Comm100 supports Agent SSO via JWT (JSON Web Token). If a user is authenticated by an identity provider via JWT, they can securely access the Comm100 account without providing separate login credentials.
To complete the Comm100 Agent SSO process, we need the cooperation of the third-party system technicians to provide the following necessary information.
-
JWT Certificate- Required, the JWT Certificate that Comm100 can verify the validity of token. It can be a symmetric encrypted secret key or an asymmetric encrypted public key. -
JWT Authentication URL- optional, the JWT Authentication URL for your JWT service that Comm100 will redirect your agents to for remote authentication.
To provide JWT Certificate
symmetric encrypted secret key- Can be any random string.
asymmetric encrypted public key- A pair of RSA PKCS#8 public and private keys are required for signing. You can generate them with the online generation tool.https://www.devglan.com/online-tools/rsa-encryption-decryption.
- A pair of RSA PKCS#8 public and private keys are required for signing. You can generate them with the online generation tool.https://www.devglan.com/online-tools/rsa-encryption-decryption.
To provide JWT Authentication URL
JWT authentication URL is an authentication callback address. When the client browser access Comm100 resources without authentication, Comm100 will start authenticating and redirect the page to defined JWT Authentication URL to request authentication.
In the call back process, you need generate jwt to save the third-party user information for login and pass jwt parameter to the redirect_url provided by Comm100.
Request authentication from app
During Comm100 authentication, the JWT Authentication interface of the app will be called back to request authentication.
curl https://example.com/api/jwt?redirect_url=https%3a%2f%2fdash11.comm100.io%2fapi%2fagentSSO%2fjwt%2fConsumer%3frelayState%3d********
Generating JWT
After receiving the Comm100 request, the app needs to generate a jwt to store the authentication information.
- JWT Algorithm and Token Type
Please specify HS256 as the JWT algorithm in the header of your JWT payload. HS256 indicates that this token is signed in using HMAC-SHA256.{ "typ":"JWT", "alg":"HS256" } - JWT Required Attribute
- An email address is required for Comm100 to uniquely identify the user. Using the attributes listed in the table below, you can send additional user profile data which will be synced between your user login system and Comm100.
Attribute Required Description email yes Email of the user being signed in. It is used to identify the user record in Comm100.
- An email address is required for Comm100 to uniquely identify the user. Using the attributes listed in the table below, you can send additional user profile data which will be synced between your user login system and Comm100.
- JWT generated through JWT Certificate。
- Example
private string GenerateToken(string username) { var sharedKey = WebConfigurationManager.AppSettings["SharedKey"]; var issuer = "jwt server"; var key = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(sharedKey)); var creds = new SigningCredentials(key, SecurityAlgorithms.HmacSha256Signature); var claims = new List<Claim> { new Claim("sub", "comm100"), new Claim("email", username), // Required. Comm100 will use it to match an agent in your site. new Claim("jti", Guid.NewGuid().ToString()), // Required. }; var audience = "Comm100"; var issued = DateTime.UtcNow; var expireMinutes = Convert.ToInt32(WebConfigurationManager.AppSettings["ExpireMinutes"]); var expires = issued.AddMinutes(expireMinutes); var token = new JwtSecurityToken(issuer, audience, claims, issued, expires, creds); var handler = new JwtSecurityTokenHandler(); return handler.WriteToken(token); }
To Handle the authentication request
After generating the jwt, attach the jwt as a parameter to the redirect_url and redirect to the redirect_url.
HTTP/1.1 302 REDIRECT
location: https://dash11.comm100.io/api/agentSSO/jwt/Consumer?relayState=********&jwt=*********
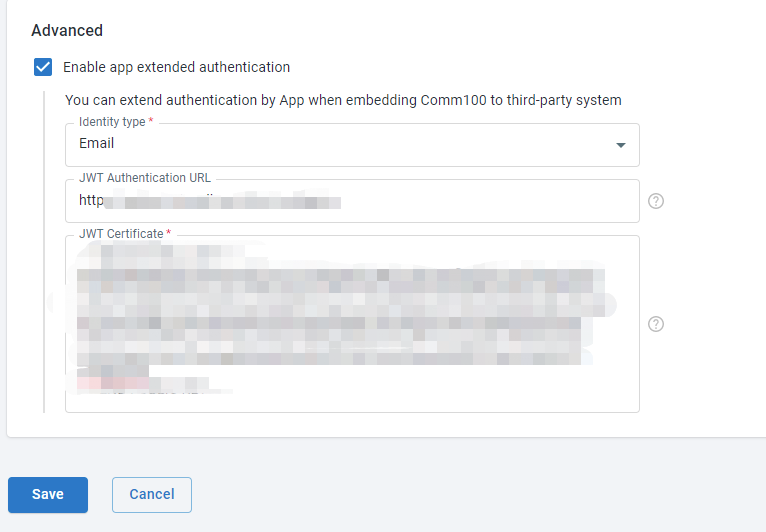
Completing app extended authentication configuration in your Comm100 Account
Through the above steps, we have learned how to fill in JWT certificate and JWT authentication URL, complete the configuration and save the changes.
Adding Comm100 into your app
Add a component that displays the Comm100 page in your application, and judge whether you have logged in before displaying it. If not, start authenticating.
Logging into your app and access Comm100 resource
After configuring the relevant configurations of Extend Authentication, you can access the resources of Comm100 by logging in to the configured application without providing separate login credentials.
Summary
Here we give a brief overview of the background, principle, steps and technical implementation details of extend authentication by apps. You may still have some questions. You can click Tutorial: Add Comm100 into Vincall to view more information. You can integrate your app into Comm100 system step by step according to the guide there.